

HIPAA Risk Analysis
A risk analysis is Required by law for covered entities. § 164.308(a)(1)(ii)(A) A covered entity is to conduct an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected health information held by the entity.
We can help to prevent costly fines, with a hands on approach, by creating a HIPAA treatment plan for you. Once the analysis is completed, we can work together to resolve the issues that we find.
Encrypted Communication
Under HIPAA Security Rules, Access Controls (§ 164.312 (a)(1)(a)), Audit Controls (§ 164.312 (a)(1)(b)), and Transmission security (§ 164.312 (a)(1)(e)), it is considered both appropriate and reasonable to protect ePHI. Therefore using an encrypted method to send ePHI would be considered required.
We have several options to solve your encrypted communication needs. The VTG synced tool is easy to use, secure, dropbox style solution that has audit logs. We also have encrypted email with a no hassle policy based encryption that also has audit logs.

Business Continuity
HIPAA Security Rule § 164.308 (a)(7) states that you must establish policies and procedures for responding to an emergency or other occurrence (for example, fire, vandalism, system failure, and natural disaster) that damages systems that contain electronic protected health information.
Our monitored Backup and Recovery solutions protects your business from any disaster including human nature. Don’t wait till something bad happens to protect you business contact us today to get started.
Smart Logon & SSO
HIPAA Security Rule, § 164.312 states that a covered entity is required to assign a unique name and/or number for identifying and tracking user identity. Implement procedures to verify that a person or entity seeking access to electronic protected health information is the one claimed. Maintain audit controls by implementing hardware, software, and/or procedural mechanisms that record and examine activity in information systems that contain or use electronic protected health information. Implement electronic procedures that terminate an electronic session after a predetermined time of inactivity.
Shared logons with common password are a security risk without a verifiable way to determine who accessed ePHI. With our smart logon technology your staff will have a unique identifier and be able to quickly logon and lock systems that have access to ePHI. Our system has the ability to track users logon, logout, and lock times complying with the HIPAA security rules. When a computer is locked by the user or by an inactivity time out and any user taps in the screen is exactly how it was left before it was locked. There is also a Single Sign On (SSO) function where the user can logon to their practice management, insurance web sites, and more with the tap of their access card or token.
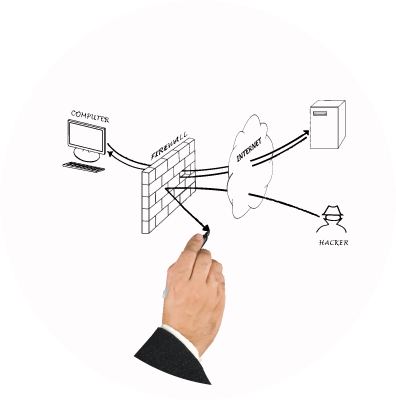
Firewalls
§ 164.308 (a)(1)(ii)(b) Implement security measures sufficient to reduce risks and vulnerabilities to a reasonable and appropriate level to comply with § 164.306(a). Ensure the confidentiality, integrity, and availability of all electronic protected health information the covered entity or business associate creates, receives, maintains, or transmits.
It is important to maintain a firewall that is HIPAA compliant. A consumer grade firewall will not properly protect you from threats or fines. Let us help you determine if your firewall meets your needs.
Antivirus
§ 164.308 (a)(1)(ii)(b) Implement security measures sufficient to reduce risks and vulnerabilities to a reasonable and appropriate level to comply with § 164.306(a). Protect against any reasonably anticipated threats or hazards to the security or integrity of such information. § 164.308 (a)(5)(ii)(b) Implement procedures for guarding against, detecting, and reporting malicious software.
Not all antivirus software is created equal. We use a managed, and monitored antivirus solution that is constantly ranked at the top of independent test labs lists. If you are using a “free” antivirus you are likely violating the license agreement or are not really protected. Let us help you determine if you are protected and in compliance with the law.


Instant Messaging
Transmission security. § 164.312 (a)(1)(e)(1) Implement technical security measures to guard against unauthorized access to electronic protected health information that is being transmitted over an electronic communications network.
Instant messaging apps like Yahoo messenger and Skype are not only not secure but also a conduit to infect computer systems and provide unauthorized access to ePHI. There are several solutions to this problem. 1st use an internal messaging application that does not use a public server to transfer messages. 2nd use a secure messaging application. We offer both types of solutions and can simplify the install and configuration for you.
Encryption
§ 164.312(e)(2)(ii) “Implement a mechanism to encrypt electronic protected health information whenever deemed appropriate.”
Do you use portable devices to access ePHI? In the event a computer, hard drive, phone, tablet, laptop or USB data device is stolen would your data be accessible to thieves? Most HIPAA fines levied as of today are from audits stemming from a lost laptop or portable device. We can help to protect your data with encryption.


Device Disposal
§ 164.312(d)(2)(i) Implement policies and procedures to address the final disposition of electronic protected health information, and/or the hardware or electronic media on which it is stored. § 164.312(d)(2)(ii) Implement procedures for removal of electronic protected health information from electronic media before the media are made available for re-use.
We offer disposal or sanitation of your old Servers, Desktops, Laptops, Faxes, and Portable Devices. Anything that may have contained data that you absolutely cannot afford to be recovered. We will destroy or sanitize the device where data recovery is not possible and provide you with a certificate with date, product with serial numbers and means of destruction so that you can add this to your required documentation.
Remote Access
Access authorization. § 164.308 (a)(4)(ii)(b) Implement policies and procedures for granting access to electronic protected health information, for example, through access to a workstation, transaction, program, process, or other mechanism.
Access your computers anywhere on any device with secure remote access software. This software is easy to use and unlike remote desktop and some other options it is secure and has access logs.


Audit Log Storage and Review
Information system activity review (Required). § 164.308 (a)(1)(ii)(d) Implement procedures to regularly review records of information system activity, such as audit logs, access reports, and security incident tracking reports.
Most computer logs are in a format that most people cannot even read let alone determine if there has been suspicious or unauthorized access. Also, who has time to sift through the hundreds of thousands of logs generated by your firewall, servers, workstations and Practice Management solutions? We offer an affordable and practical solution to this overwhelming problem. Our monitoring service provides easy to review monthly reports helping to comply with this portion of the HIPAA security rules when it comes to log access review.
Web Content Filter
§ 164.308 (a)(5)(ii)(b) Implement procedures for guarding against, detecting, and reporting malicious software.
Protect your business from legal liability and reduce the risk of a security breach through proactive internet access controls. Block your users from visiting suspected and confirmed unsafe sites and keep them productive with common-sense web browsing policies designed for the workplace. Our solution is complete with detailed reporting tools that let you analyze browsing activity and demonstrate the effectiveness of web security.


Mobile Device Tracking & Remote Wipe
Access authorization. § 164.308 (a)(4)(ii)(b) Implement policies and procedures for granting access to electronic protected health information, for example, through access to a workstation, transaction, program, process, or other mechanism.
Protect your mobile devices against theft and loss with location tracking, remote lock, change pass code and, remote wipe. It’s too late once your device has been lost. Be prepared and give yourself and law enforcement a fighting chance to recover your mobile devices. We have personally been successful in recovering stolen devices.
Business Associate Identification
Implementation specifications: Written contract or other arrangement (Required). § 164.308 (b)(3) Document the satisfactory assurances required by paragraph (b)(1) or (b)(2) of this section through a written contract or other arrangement with the business associate that meets the applicable requirements of § 164.314(a).
Let us help you audit your network and business practices to identify products that you are using that need a Business Associate agreement on file. According to the OCR if you don’t have a signed BAA with your provider that claims that they are HIPAA compliant then the products you are using CANNOT be HIPAA compliant. It’s better to be safe with a review like this and it’s even better because we offer this service FREE of charge.

HIPPA Risk Analysis
A risk analysis is Required by law for covered entities. § 164.308(a)(1)(ii)(A) A covered entity is to conduct an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected health information held by the entity.
We can help to prevent costly fines, with a hands on approach, by creating a HIPPA treatment plan for you. Once the analysis is completed, we can work together to resolve the issues that we find.

Encrypted Communication
Under HIPAA Security Rules, Access Controls (§ 164.312 (a)(1)(a)), Audit Controls (§ 164.312 (a)(1)(b)), and Transmission security (§ 164.312 (a)(1)(e)), it is considered both appropriate and reasonable to protect ePHI. Therefore using an encrypted method to send ePHI would be considered required.
We have several options to solve your encrypted communication needs. The VTG synced tool is easy to use, secure, dropbox style solution that has audit logs. We also have encrypted email with a no hassle policy based encryption that also has audit logs.

Business Continuity
Hippa Security Rule § 164.308 (a)(7) states that you must establish policies and procedures for responding to an emergency or other occurrence (for example, fire, vandalism, system failure, and natural disaster) that damages systems that contain electronic protected health information.
Our monitored Backup and Recovery solutions protects your business from any disaster including human nature. Don’t wait till something bad happens to protect you business contact us today to get started.

Smart Logon & SSO
HIPAA Security Rule, § 164.312 states that a covered entity is required to assign a unique name and/or number for identifying and tracking user identity. Implement procedures to verify that a person or entity seeking access to electronic protected health information is the one claimed. Maintain audit controls by implementing hardware, software, and/or procedural mechanisms that record and examine activity in information systems that contain or use electronic protected health information. Implement electronic procedures that terminate an electronic session after a predetermined time of inactivity.
Shared logons with common password are a security risk without a verifiable way to determine who accessed ePHI. With our smart logon technology your staff will have a unique identifier and be able to quickly logon and lock systems that have access to ePHI. Our system has the ability to track users logon, logout, and lock times complying with the HIPPA security rules. When a computer is locked by the user or by an inactivity time out and any user taps in the screen is exactly how it was left before it was locked. There is also a Single Sign On (SSO) function where the user can logon to their practice management, insurance web sites, and more with the tap of their access card or token.


